Public key infrastructure is a key part of your everyday interaction in the cyber world. It secures all your activities over the internet- from the login credentials in your browser to the sensitive data you share via email. Especially for electronic transactions, it is critical to electronically identify people and machines in a reliable way.
Also, when it comes to securing a partnership with a business, a Public Key Infrastructure or PKI is highly recommended. Here is why!
Firstly, let us go through what is PKI.
What is PKI?
A PKI is a Cryptosystem, in other words, a particular security service that is used to achieve confidentiality. There are 3 terms related to security, or a triad, of terms necessary which go by the acronym “CIA” – confidentiality, integrity, and availability.
- Confidentiality: Ability to hide information from unauthorized access.
- Integrity: Maintain consistency, accuracy, and trustworthiness of data over the entire lifecycle.
- Availability: Information requested is readily available to authorized identity.
Public key infrastructure is a system based on encryption key pairs and digital certificates and is used for securing communications between different computer systems. It’s also a system that helps organizations to remain compliant with regulatory data security and privacy requirements and avoid penalties, fines, and reputational loss.
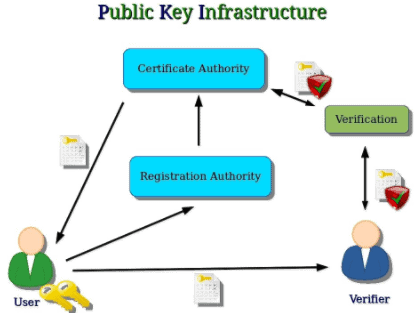
The Keys
As mentioned, there are a pair of keys. Now, in terms of security, a Key is a long string of bits that can be used to encrypt data. The two keys are a public key and a private key. From the name, the Public key is meant for the public, meaning it can be distributed to different people. As for the Private key, it is meant to be kept confidential and should not get into the hands of anyone but the person who has the key.
What is the purpose of these keys? Well, in short, they are needed to prevent something from being transmitted between two parties from being intercepted. In other words, to avoid the loss, or breaching of a transfer of messages between two parties. Such invasion is called “Man in the Middle” attacks, or MITM attacks, which are generally subtle and can tamper with the information being transmitted.
Certificate & Authority
PKI Certificates are digital “passports”, or data packages, that can help identify the authenticity of the party that is associated with the public key. The digital certificate is encrypted through asymmetric cryptography, itself. This is done with the help of a CA, or Certificate Authority. What does the CA do?
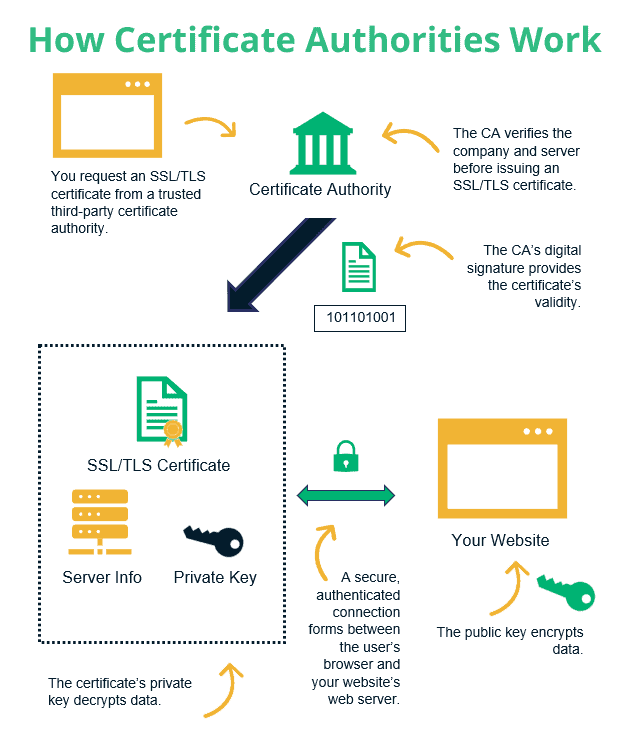
The Certificate Authority is a set of IT system, as well as an organization which is responsible for issuing, revoking, and distributing digital certificates. A CA is usually a 3rd party organization that is trusted by all the parties which participate in a PKI, such as Microsoft Certification Authority, or Microsoft CA. A CA verifies the identity of the party requesting a certificate as well as the public key of the participating party in their respective certificate.
Benefits of Having a Good PKI System in Place
The cornerstone of every PKI is trust. When delivering a digital certificate, using a trustworthy third party (CA) vouch for the sender, it is to assure the recipient that the sender is who they are.
Here are some key benefits of a good PKI system in place:
- Internal communications, such as database servers, are secured.
- Local Area Networks are more secured especially with PKI being built-in to Microsoft Active Directory which allows smart & physical “key” cards to verify user identity.
- It allows emails to be more encrypted from any account hijacking or eavesdropping.
Kidan helps implement the best cybersecurity solutions for business applications to protect personal and confidential data in high-class security systems. Click Here to learn more about our cybersecurity services.
You can find more information below:
Kidan’s Contact Information:
Email: [email protected]
Phone Number: +41 22 519 64 01
Connect with us:
LinkedIn: https://www.linkedin.com/company/kidanch/about/
Twitter: https://twitter.com/Kidan_Global
Medium: https://medium.com/@kidan
Facebook: https://www.facebook.com/kidan.ch/
Instagram: https://www.instagram.com/kidanllc/


